Port Mirroring Complete Guide 2025: Network Traffic Analysis, SPAN Configuration & Best Practices
Table of Contents
- What is Port Mirroring? Definition and Overview
- How Port Mirroring Works: Technical Deep Dive
- Types of Port Mirroring Solutions
- Port Mirroring Benefits for Network Monitoring
- Port Mirroring Limitations and Challenges
- Port Mirroring vs Traffic Mirroring: Complete Comparison
- Step-by-Step Configuration Guides
- Advanced Port Mirroring Techniques
- Port Mirroring Tools and Software
- Troubleshooting Common Port Mirroring Issues
- Security Considerations for Port Mirroring
- Industry Use Cases and Case Studies
- Port Mirroring Best Practices
- Future of Network Traffic Mirroring
- Frequently Asked Questions
What is Port Mirroring? Definition and Overview
Port mirroring (also known as SPAN - Switched Port Analyzer) is a network switch feature that creates exact copies of network traffic from one or more source ports and forwards them to a designated destination port for monitoring and analysis. This network monitoring technique enables administrators to observe network communications without disrupting the original data flow.
Port mirroring serves as the foundation for network troubleshooting, security monitoring, compliance auditing, and performance optimization in enterprise environments. Unlike network taps or inline monitoring devices, port mirroring operates entirely within the switch infrastructure, making it a cost-effective solution for network visibility.
Key Port Mirroring Components
- Source Port(s): The network port(s) whose traffic is being monitored
- Destination Port: The mirror port where copied traffic is sent
- Mirror Session: The configuration that defines the mirroring relationship
- Traffic Direction: Ingress, egress, or bidirectional traffic copying
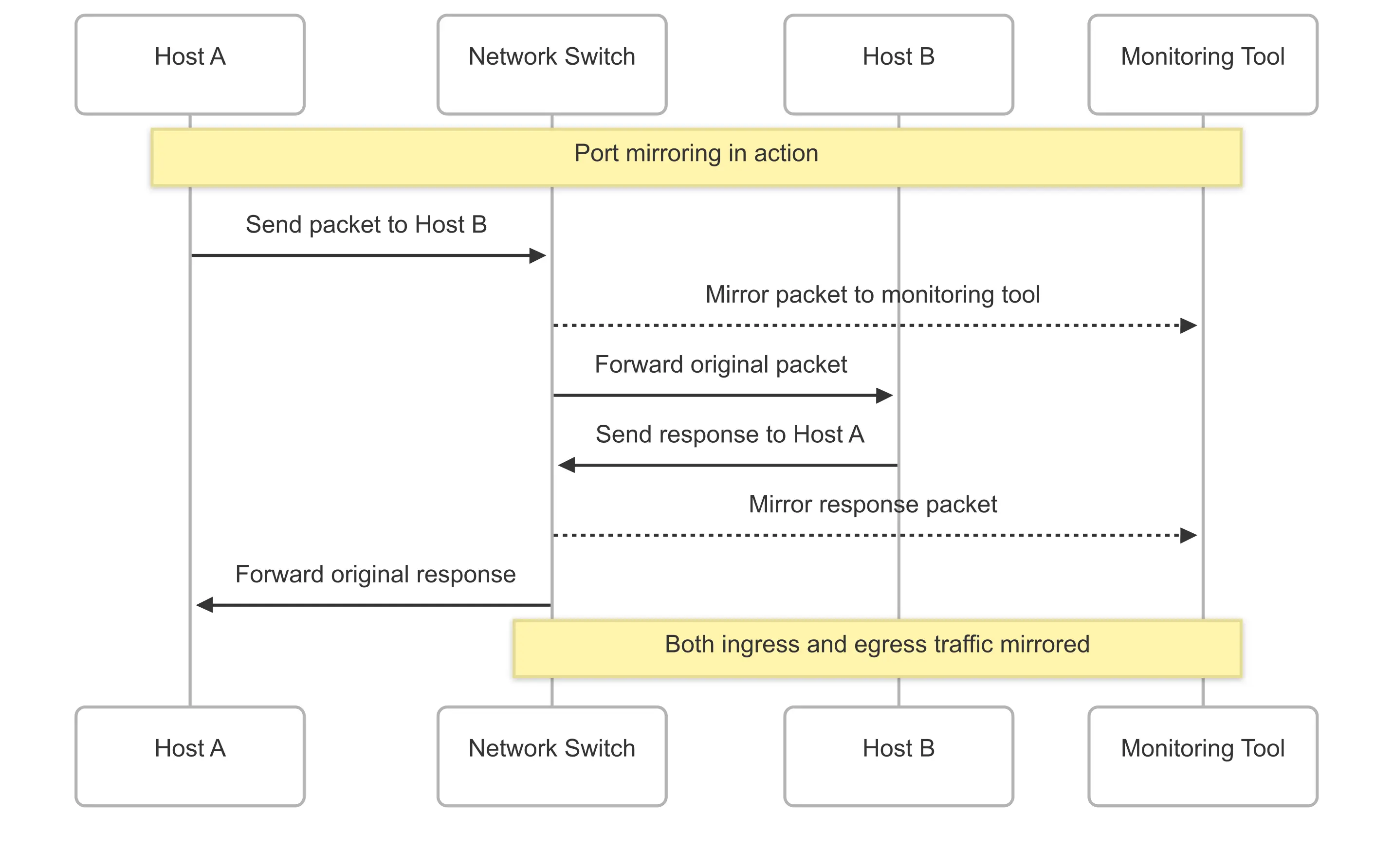
How Port Mirroring Works: Technical Deep Dive
Port mirroring operates at the data link layer (Layer 2) of the OSI model, intercepting packets as they traverse switch ports. When a packet arrives at or departs from a monitored port, the switch’s ASIC (Application-Specific Integrated Circuit) creates an identical copy and forwards it to the configured mirror port.
Port Mirroring Architecture
[Source Device] ←→ [Switch Port 1 (Source)] ←→ [Destination Device]
↓ (Traffic Copy)
[Mirror Port] → [Network Analyzer]Traffic Flow Process
- Packet Reception: Switch receives traffic on source port
- Packet Processing: Normal switching logic processes the original packet
- Mirror Copy Creation: Switch ASIC creates an identical packet copy
- Mirror Forwarding: Copy is queued for transmission to mirror port
- Analysis: Monitoring tool receives and analyzes the mirrored traffic
Port Mirroring Sequence Diagram
The mirroring process occurs simultaneously with normal packet forwarding, ensuring minimal impact on network performance while providing complete traffic visibility.
Types of Port Mirroring Solutions
1. Local Port Mirroring (SPAN)
Local SPAN mirrors traffic between ports on the same physical switch, making it the simplest form of port mirroring implementation.
Characteristics:
- Source and destination ports on same switch
- No network overhead for mirror traffic transport
- Limited to single-switch visibility
- Easiest configuration and troubleshooting
Use Cases:
- Small office network monitoring
- Single-server traffic analysis
- Basic security monitoring
- Development environment testing
2. Remote Port Mirroring (RSPAN)
Remote SPAN extends mirroring capabilities across multiple switches using VLANs to transport mirrored traffic throughout the network infrastructure.
Characteristics:
- Cross-switch traffic mirroring
- Uses dedicated RSPAN VLAN for traffic transport
- Requires RSPAN-capable switches in path
- Centralized monitoring capabilities
Configuration Requirements:
- RSPAN VLAN creation on all participating switches
- Trunk port configuration for RSPAN VLAN transport
- Consistent RSPAN VLAN ID across network
3. Encapsulated Remote Port Mirroring (ERSPAN)
ERSPAN uses GRE (Generic Routing Encapsulation) tunneling to transport mirrored traffic over Layer 3 networks, enabling monitoring across WAN connections and data centers.
Advanced Features:
- Layer 3 routing for mirror traffic
- GRE tunnel encapsulation
- Cross-datacenter monitoring capabilities
- IP-based destination addressing
Benefits:
- No VLAN infrastructure requirements
- Routing-based traffic transport
- Enhanced scalability options
- Multi-site monitoring support
4. Flow-Based Port Mirroring
Modern switches support flow-based mirroring that selectively mirrors traffic based on specific criteria such as source/destination IP addresses, protocols, or application types.
Selection Criteria:
- IP address ranges
- Protocol types (TCP, UDP, ICMP)
- Port numbers
- VLAN membership
- Quality of Service (QoS) markings
Port Mirroring Benefits for Network Monitoring
Non-Intrusive Network Analysis
Port mirroring provides passive monitoring capabilities without introducing any latency or disruption to production traffic. This non-intrusive approach ensures that business-critical applications continue operating normally while administrators gain complete visibility into network communications.
Real-Time Packet Inspection
Deep packet inspection becomes possible through port mirroring, enabling administrators to analyze packet headers, payloads, and protocol behavior in real-time. This capability is essential for:
- Application performance troubleshooting
- Security threat detection
- Protocol compliance verification
- Network optimization initiatives
Comprehensive Security Monitoring
Port mirroring enables deployment of intrusion detection systems (IDS) and intrusion prevention systems (IPS) without inline network placement. Security benefits include:
- Malware detection and analysis
- Unauthorized access monitoring
- Data exfiltration prevention
- Compliance violation detection
Network Forensics and Compliance
Many regulatory frameworks require network traffic monitoring and logging. Port mirroring supports compliance with:
- PCI-DSS: Payment card industry security standards
- HIPAA: Healthcare information privacy requirements
- SOX: Financial reporting and auditing standards
- GDPR: Data protection and privacy regulations
Application Performance Optimization
Port mirroring enables application performance monitoring (APM) by providing visibility into:
- Database query response times
- Web application transaction flows
- API call latencies
- Microservices communication patterns
Port Mirroring Limitations and Challenges
Switch Resource Consumption
Port mirroring consumes significant switch resources, including:
- CPU utilization for packet copying operations
- Memory buffers for mirror packet queuing
- ASIC processing power for simultaneous packet handling
- Backplane bandwidth for internal traffic transport
Mirror Port Bandwidth Limitations
The destination mirror port must have sufficient bandwidth to handle all mirrored traffic. Common issues include:
- Port speed mismatches between source and mirror ports
- Traffic aggregation when mirroring multiple high-speed ports
- Burst traffic handling during peak utilization periods
- Packet dropping when mirror port becomes saturated
Encrypted Traffic Analysis Challenges
Modern networks extensively use encryption, limiting port mirroring effectiveness for:
- TLS/SSL encrypted communications
- VPN tunnel traffic analysis
- Application-layer encryption protocols
- End-to-end encrypted messaging
Scalability Constraints
Port mirroring faces scalability challenges in large networks:
- Limited mirror sessions per switch
- Hardware resource exhaustion under high load
- Network topology complexity for remote mirroring
- Management overhead for multiple mirror configurations
Port Mirroring vs Traffic Mirroring: Complete Comparison
| Aspect | Traditional Port Mirroring | Cloud Traffic Mirroring |
|---|---|---|
| Deployment Environment | Physical network switches | Cloud virtual networks (VPC) |
| Implementation Method | Hardware-based SPAN/RSPAN | Software-defined networking |
| Traffic Scope | Switch port level | Instance/subnet level |
| Encapsulation Protocol | VLAN tagging, GRE tunneling | VPC-native encapsulation |
| Scalability | Hardware resource limited | Elastically scalable |
| Cost Structure | Switch licensing/hardware | Usage-based cloud pricing |
| Management Interface | CLI/SNMP configuration | Cloud management console |
| Integration Options | Traditional monitoring tools | Cloud-native analytics services |
| Geographic Distribution | Limited by network topology | Global cloud infrastructure |
| Automation Capabilities | Script-based configuration | API-driven orchestration |
When to Choose Port Mirroring
- Physical datacenter environments
- Existing network infrastructure
- Hardware-based security appliances
- Regulatory compliance requirements
- Cost-sensitive implementations
When to Choose Cloud Traffic Mirroring
- Cloud-native applications
- Multi-region deployments
- Elastic scaling requirements
- DevOps automation integration
- Advanced analytics capabilities
Step-by-Step Configuration Guides
Cisco Switch Port Mirroring Configuration
Basic Local SPAN Configuration
! Enter global configuration mode
Switch# configure terminal
! Configure monitor session 1 with source interface
Switch(config)# monitor session 1 source interface GigabitEthernet1/0/1
! Set destination interface for mirror traffic
Switch(config)# monitor session 1 destination interface GigabitEthernet1/0/24
! Optional: Configure traffic direction (rx = ingress, tx = egress, both = default)
Switch(config)# monitor session 1 source interface GigabitEthernet1/0/1 rx
! Save configuration
Switch(config)# end
Switch# write memoryAdvanced SPAN Configuration with Filtering
! Configure SPAN with VLAN filtering
Switch(config)# monitor session 2 source interface range GigabitEthernet1/0/1-5
Switch(config)# monitor session 2 filter vlan 10,20,30
Switch(config)# monitor session 2 destination interface GigabitEthernet1/0/48
! Configure SPAN with ACL filtering
Switch(config)# ip access-list extended SPAN_FILTER
Switch(config-ext-nacl)# permit tcp any host 192.168.1.100
Switch(config-ext-nacl)# exit
Switch(config)# monitor session 3 source interface GigabitEthernet1/0/10
Switch(config)# monitor session 3 filter ip access-group SPAN_FILTER
Switch(config)# monitor session 3 destination interface GigabitEthernet1/0/47Remote SPAN (RSPAN) Configuration
! Configure RSPAN VLAN on all participating switches
Switch(config)# vlan 999
Switch(config-vlan)# name RSPAN_VLAN
Switch(config-vlan)# remote-span
Switch(config-vlan)# exit
! Source switch configuration
SourceSwitch(config)# monitor session 1 source interface GigabitEthernet1/0/5
SourceSwitch(config)# monitor session 1 destination remote vlan 999
! Destination switch configuration
DestSwitch(config)# monitor session 1 source remote vlan 999
DestSwitch(config)# monitor session 1 destination interface GigabitEthernet1/0/24Juniper Switch Configuration
Basic Port Mirroring Setup
# Configure analyzer for port mirroring
set analyzer port-mirror input ingress interface ge-0/0/1
set analyzer port-mirror input egress interface ge-0/0/1
set analyzer port-mirror output interface ge-0/0/24
# Commit configuration
commitAdvanced Filtering Configuration
# Configure port mirroring with packet filtering
set analyzer advanced-mirror input ingress interface ge-0/0/5
set analyzer advanced-mirror input ingress interface ge-0/0/6
set analyzer advanced-mirror output interface ge-0/0/48
set analyzer advanced-mirror loss-priority low
set analyzer advanced-mirror ratio 10
# Apply firewall filter for selective mirroring
set firewall family inet filter MIRROR_FILTER term WEB_TRAFFIC from protocol tcp
set firewall family inet filter MIRROR_FILTER term WEB_TRAFFIC from port 80
set firewall family inet filter MIRROR_FILTER term WEB_TRAFFIC then port-mirror
set firewall family inet filter MIRROR_FILTER term WEB_TRAFFIC then acceptHP/Aruba Switch Configuration
Basic Mirror Configuration
; Configure port mirroring session
mirror 1 name "WebServer_Monitor"
mirror 1 port A1 monitor-port A24
; Configure bidirectional mirroring
mirror 2 port A5 both monitor-port A23
; Save configuration
write memoryVLAN-Based Mirroring
; Configure VLAN mirroring
mirror 3 vlan 100 monitor-port A22
mirror 3 name "VLAN100_Security_Monitor"
; Configure multiple VLAN mirroring
mirror 4 vlan 10,20,30 monitor-port A21Advanced Port Mirroring Techniques
Load Balancing Mirror Traffic
For high-throughput environments, distribute mirror traffic across multiple destination ports:
! Configure multiple mirror sessions for load distribution
Switch(config)# monitor session 1 source interface range Gi1/0/1-10
Switch(config)# monitor session 1 destination interface Gi1/0/47
Switch(config)# monitor session 2 source interface range Gi1/0/11-20
Switch(config)# monitor session 2 destination interface Gi1/0/48Selective Protocol Mirroring
Mirror only specific protocols to reduce traffic volume:
! Create ACL for HTTP/HTTPS traffic only
Switch(config)# ip access-list extended WEB_TRAFFIC
Switch(config-ext-nacl)# permit tcp any any eq 80
Switch(config-ext-nacl)# permit tcp any any eq 443
Switch(config-ext-nacl)# exit
! Apply ACL to mirror session
Switch(config)# monitor session 5 source interface Gi1/0/15
Switch(config)# monitor session 5 filter ip access-group WEB_TRAFFIC
Switch(config)# monitor session 5 destination interface Gi1/0/46Time-Based Mirror Activation
Implement scheduled mirroring for specific monitoring windows:
! Create time-range for business hours monitoring
Switch(config)# time-range BUSINESS_HOURS
Switch(config-time-range)# periodic weekdays 8:00 to 18:00
Switch(config-time-range)# exit
! Apply time-based ACL to mirror session
Switch(config)# ip access-list extended BUSINESS_MONITOR
Switch(config-ext-nacl)# permit ip any any time-range BUSINESS_HOURS
Switch(config-ext-nacl)# exit
Switch(config)# monitor session 6 filter ip access-group BUSINESS_MONITORPort Mirroring Tools and Software
Network Analysis Tools
Wireshark
- Free, open-source packet analyzer
- Cross-platform support (Windows, macOS, Linux)
- Deep protocol analysis with 3000+ protocol dissectors
- Real-time capture and offline analysis capabilities
- Powerful filtering and search functionality
tcpdump
- Command-line packet analyzer for Unix/Linux systems
- Lightweight and efficient for high-volume capture
- Scriptable interface for automated analysis
- Low resource consumption suitable for production environments
Zeek (formerly Bro)
- Network security monitoring platform
- Protocol analysis and anomaly detection
- Scripting language for custom analysis logic
- Log generation for SIEM integration
Commercial Monitoring Platforms
SolarWinds Network Performance Monitor
- Comprehensive network monitoring with SPAN integration
- Real-time alerting and performance tracking
- Customizable dashboards and reporting
- Integration capabilities with other SolarWinds tools
PRTG Network Monitor
- All-in-one monitoring solution with packet capture
- Web-based interface for easy management
- Automated discovery and configuration
- Flexible alerting and notification options
ManageEngine OpManager
- Enterprise network monitoring with traffic analysis
- Multi-vendor device support for diverse environments
- Performance baseline establishment and deviation alerts
- Compliance reporting for regulatory requirements
Cloud-Native Solutions
AWS VPC Traffic Mirroring
- Native AWS integration with EC2 and VPC
- Elastic scaling based on traffic volume
- Integration with AWS security services (GuardDuty, Security Hub)
- Cost-optimized pay-per-use pricing model
Azure Network Watcher
- Packet capture capabilities for Azure VMs
- Network topology visualization and monitoring
- Connection troubleshooting and diagnostic tools
- Integration with Azure Monitor and Log Analytics
Troubleshooting Common Port Mirroring Issues
Mirror Port Oversubscription
Problem: Mirror port drops packets due to insufficient bandwidth
Symptoms:
- Incomplete packet capture in analysis tools
- High utilization on mirror port
- Intermittent traffic visibility gaps
Solutions:
! Check mirror port utilization
Switch# show interface GigabitEthernet1/0/24 | include rate
! Configure traffic sampling to reduce volume
Switch(config)# monitor session 1 source interface Gi1/0/10 sampling-rate 4096
! Use multiple mirror ports for load distribution
Switch(config)# monitor session 1 destination interface Gi1/0/47-48RSPAN VLAN Issues
Problem: RSPAN traffic not reaching destination switch
Troubleshooting Steps:
! Verify RSPAN VLAN configuration
Switch# show vlan id 999
! Check trunk configuration on intermediate switches
Switch# show interface trunk | include 999
! Verify RSPAN session status
Switch# show monitor session 1Common Fixes:
! Ensure RSPAN VLAN is allowed on all trunk ports
Switch(config)# interface range GigabitEthernet1/0/23-24
Switch(config-if-range)# switchport trunk allowed vlan add 999
! Configure RSPAN VLAN as remote-span on all switches
Switch(config)# vlan 999
Switch(config-vlan)# remote-spanSwitch Resource Exhaustion
Problem: Switch performance degradation during mirroring
Monitoring Commands:
! Check CPU utilization
Switch# show processes cpu sorted
! Monitor memory usage
Switch# show memory statistics
! Verify mirror session resource usage
Switch# show monitor session all detailOptimization Strategies:
- Implement selective mirroring with ACLs
- Use sampling rates for high-volume ports
- Schedule mirroring during off-peak hours
- Upgrade switch hardware if necessary
Packet Timestamp Accuracy
Problem: Inaccurate timestamps affecting analysis
Solutions:
! Configure NTP for accurate time synchronization
Switch(config)# ntp server 192.168.1.10
! Enable hardware timestamping if supported
Switch(config)# monitor session 1 destination interface Gi1/0/24 encapsulation dot1q 100 ingress dot1q vlan 100Security Considerations for Port Mirroring
Mirror Port Access Control
Protect mirror ports from unauthorized access to prevent security breaches:
! Configure port security on mirror port
Switch(config)# interface GigabitEthernet1/0/24
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security maximum 1
Switch(config-if)# switchport port-security mac-address sticky
Switch(config-if)# switchport port-security violation shutdownEncrypted Traffic Handling
Implement proper procedures for encrypted traffic analysis:
- SSL/TLS Decryption: Use appropriate certificates and keys
- Key Management: Secure storage and rotation of decryption keys
- Privacy Compliance: Ensure monitoring complies with privacy regulations
- Data Retention: Implement appropriate data retention and deletion policies
Administrative Access Security
Secure switch management interfaces used for mirror configuration:
! Configure secure management access
Switch(config)# ip ssh version 2
Switch(config)# line vty 0 15
Switch(config-line)# transport input ssh
Switch(config-line)# login local
Switch(config-line)# exit
! Implement RBAC for mirror configuration
Switch(config)# username netadmin privilege 15 secret SecurePassword123
Switch(config)# privilege exec level 10 monitor sessionData Privacy and Compliance
Ensure port mirroring implementations comply with relevant regulations:
- GDPR Article 32: Technical and organizational security measures
- HIPAA Security Rule: Electronic protected health information safeguards
- PCI-DSS Requirement 2: Vendor-supplied defaults and security parameters
- SOX Section 404: Internal control over financial reporting
Industry Use Cases and Case Studies
Financial Services: Trading Floor Monitoring
Challenge: Monitor high-frequency trading communications for compliance
Solution: Implemented ERSPAN across multiple trading floors with microsecond timestamp accuracy
Results:
- 99.99% packet capture accuracy
- Sub-microsecond timestamp precision
- Automated compliance reporting
- Reduced audit preparation time by 60%
Healthcare: HIPAA Compliance Monitoring
Challenge: Monitor patient data access across hospital network
Solution: Deployed selective port mirroring with encrypted traffic analysis
Implementation:
! Mirror only database server traffic
Switch(config)# monitor session 1 source interface Gi1/0/15
Switch(config)# ip access-list extended HIPAA_MONITOR
Switch(config-ext-nacl)# permit tcp any host 10.1.100.50 eq 1433
Switch(config-ext-nacl)# permit tcp host 10.1.100.50 eq 1433 any
Switch(config)# monitor session 1 filter ip access-group HIPAA_MONITORResults:
- Complete database access audit trail
- Automated HIPAA violation detection
- 95% reduction in manual log review
- Improved patient data security posture
E-commerce: DDoS Attack Mitigation
Challenge: Real-time detection and mitigation of distributed denial-of-service attacks
Solution: Implemented high-speed port mirroring with ML-based anomaly detection
Architecture:
- 10Gbps mirror ports for high-volume capture
- Real-time stream processing for attack pattern detection
- Automated mitigation through dynamic ACL deployment
- Integration with CDN and upstream ISP filtering
Results:
- 30-second attack detection time
- 99.9% uptime during attack campaigns
- 70% reduction in false positive alerts
- Proactive threat intelligence gathering
Port Mirroring Best Practices
Design and Planning
Network Topology Assessment
- Document existing infrastructure including switch models and capabilities
- Identify critical monitoring points based on security and compliance requirements
- Plan mirror port placement for optimal coverage and accessibility
- Assess bandwidth requirements for mirror traffic transport
Capacity Planning
! Calculate mirror traffic volume
Total Mirror Traffic = Σ(Source Port Utilization × Number of Directions)
! Example calculation for 4 × 1Gbps ports at 60% utilization
Mirror Traffic = 4 × 1Gbps × 0.6 × 2 (bidirectional) = 4.8Gbps
Required Mirror Port = 10Gbps (minimum)Implementation Guidelines
Phased Deployment Approach
- Pilot Phase: Deploy on non-critical network segments
- Testing Phase: Validate mirror accuracy and switch performance
- Production Rollout: Implement across critical infrastructure
- Optimization Phase: Fine-tune configurations based on operational data
Configuration Standards
! Standard naming convention for mirror sessions
monitor session [LOCATION]_[PURPOSE]_[ID] source interface [SOURCE]
monitor session DATACENTER_SECURITY_01 destination interface [DEST]
! Documentation template
! Mirror Session: DATACENTER_SECURITY_01
! Purpose: Security monitoring for web servers
! Source: GigabitEthernet1/0/10-15 (Web server farm)
! Destination: GigabitEthernet1/0/48 (Security appliance)
! Created: 2025-01-15 by John Smith
! Last Modified: 2025-01-15 by John SmithOperational Management
Monitoring and Alerting
! Configure SNMP monitoring for mirror sessions
Switch(config)# snmp-server enable traps span
Switch(config)# snmp-server host 192.168.1.100 version 2c public
! Create EEM script for mirror port utilization alerting
Switch(config)# event manager applet MIRROR_PORT_ALERT
Switch(config-applet)# event snmp oid 1.3.6.1.2.1.2.2.1.10.48 get-type next entry-op ge entry-val 800000000 poll-interval 30
Switch(config-applet)# action 1.0 syslog msg "Mirror port utilization exceeding 80%"
Switch(config-applet)# action 2.0 mail server "192.168.1.200" to "[email protected]" from "[email protected]" subject "Mirror Port Alert"Change Management
- Configuration backup before mirror session modifications
- Impact assessment for new mirror session implementations
- Rollback procedures in case of performance issues
- Documentation updates for all configuration changes
Performance Optimization
Traffic Filtering Strategies
! Time-based filtering for peak hour monitoring
ip access-list extended PEAK_HOURS_ONLY
permit ip any any time-range BUSINESS_HOURS
time-range BUSINESS_HOURS
periodic weekdays 9:00 to 17:00
! Application-specific filtering
ip access-list extended CRITICAL_APPS
permit tcp any any eq 443
permit tcp any any eq 993
permit tcp any any eq 22Resource Management
- Monitor switch CPU and memory utilization during mirroring
- Implement quality of service (QoS) to prioritize production traffic
- Use sampling techniques for high-volume environments
- Schedule intensive mirroring during maintenance windows
Future of Network Traffic Mirroring
Software-Defined Networking (SDN) Integration
The evolution toward SDN architectures is transforming port mirroring capabilities:
OpenFlow-Based Mirroring
# Example OpenFlow controller mirroring rule
flow_mod = {
'table_id': 0,
'match': {'in_port': 1, 'eth_type': 0x0800},
'instructions': [
{'type': 'APPLY_ACTIONS', 'actions': [
{'type': 'OUTPUT', 'port': 2}, # Forward normally
{'type': 'OUTPUT', 'port': 48} # Mirror to port 48
]}
]
}Programmable Mirroring Logic
- Dynamic mirror rule creation based on traffic patterns
- ML-driven selective mirroring for anomaly detection
- API-based configuration management for automation
- Intent-based networking integration
Cloud-Native Evolution
Container Network Mirroring
Modern containerized environments require new approaches:
# Kubernetes NetworkPolicy for traffic mirroring
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: webapp-mirror-policy
spec:
podSelector:
matchLabels:
app: webapp
policyTypes:
- Ingress
- Egress
ingress:
- from:
- podSelector:
matchLabels:
app: monitoringService Mesh Integration
- Envoy proxy sidecar traffic capture
- Istio service mesh observability features
- Distributed tracing integration
- Microservices communication analysis
Artificial Intelligence and Machine Learning
Intelligent Traffic Analysis
- Automated threat detection using supervised learning
- Behavioral anomaly identification through unsupervised learning
- Predictive analytics for capacity planning
- Natural language processing for log analysis
Autonomous Network Operations
# Example ML-based mirror configuration
class SmartMirroringSystem:
def __init__(self):
self.ml_model = load_trained_model()
def analyze_traffic_patterns(self, network_data):
predictions = self.ml_model.predict(network_data)
return self.generate_mirror_recommendations(predictions)
def auto_configure_mirroring(self, recommendations):
for config in recommendations:
self.deploy_mirror_session(config)Integration with Extended Detection and Response (XDR)
Port mirroring is evolving to support comprehensive security platforms:
- Multi-source data correlation combining network, endpoint, and cloud telemetry
- Automated incident response based on mirrored traffic analysis
- Threat hunting capabilities with historical traffic replay
- Integration with SOAR platforms for orchestrated responses
Frequently Asked Questions
General Port Mirroring Questions
Q: What is port mirroring used for in network administration?
A: Port mirroring serves multiple critical functions including network troubleshooting, security monitoring, compliance auditing, application performance analysis, and forensic investigation. It enables administrators to observe network traffic non-intrusively for diagnostic and monitoring purposes.
Q: What’s the difference between port mirroring and port forwarding?
A: Port mirroring creates copies of network traffic for monitoring without affecting the original data flow, while port forwarding redirects network connections from one IP address/port combination to another. They serve completely different purposes in network management.
Q: D oes port mirroring affect performance?
A: Yes, excessive port mirroring can impact switch performance by consuming CPU resources, memory buffers, and internal bandwidth. However, when properly configured with appropriate capacity planning, the impact is typically minimal in modern enterprise switches.
Technical Implementation Questions
Q: How do I choose the right type of port mirroring for my environment?
A: The choice depends on your network topology and monitoring requirements:
- Local SPAN: Single switch environments, simple monitoring needs
- RSPAN: Multi-switch Layer 2 networks, centralized monitoring
- ERSPAN: Layer 3 networks, WAN environments, data center interconnects
Q: What happens when mirror port bandwidth is exceeded?
A: When mirror port capacity is exceeded, packets are dropped at the mirror destination. This results in incomplete traffic capture and potential gaps in monitoring data. Solutions include using higher-speed mirror ports, implementing traffic sampling, or selective filtering.
Q: How can I monitor encrypted traffic through port mirroring?
A: While port mirroring captures encrypted traffic, the payload remains encrypted. Analysis options include:
- Monitoring connection patterns and metadata
- Using SSL/TLS decryption appliances with appropriate certificates
- Analyzing unencrypted protocol headers
- Implementing network-based application recognition (NBAR)
Configuration and Troubleshooting Questions
Q: Why is my RSPAN configuration not working?
A: Common RSPAN issues include:
- RSPAN VLAN not configured on intermediate switches
- Trunk ports not allowing RSPAN VLAN traffic
- RSPAN VLAN not marked as remote-span on all switches
- Spanning tree blocking RSPAN VLAN on some ports
Q: How many mirror sessions can I configure on a single switch?
A: This varies by switch model and manufacturer:
- Cisco Catalyst switches: Typically 2-4 local SPAN sessions, 66 RSPAN sessions
- Juniper switches: Usually 1-4 analyzer instances depending on model
- HP/Aruba switches: Generally 4-8 mirror sessions per switch
- High-end data center switches: May support 16+ concurrent sessions
Q: Can I mirror traffic from multiple VLANs simultaneously?
A: Yes, most enterprise switches support VLAN-based mirroring. You can configure mirror sessions to capture traffic from specific VLANs or ranges of VLANs:
! Mirror traffic from multiple VLANs
Switch(config)# monitor session 1 source vlan 10,20,30-40
Switch(config)# monitor session 1 destination interface Gi1/0/48Security and Compliance Questions
Q: Is port mirroring secure? Can it be a security risk?
A: Port mirroring itself can pose security risks if not properly secured:
- Unauthorized access to mirrored traffic exposes sensitive data
- Insider threats through unrestricted mirror port access
- Compliance violations if monitoring exceeds legal boundaries
- Data leakage through unsecured mirror destinations
Mitigation strategies:
- Implement physical security for mirror ports
- Use encrypted transport for remote mirroring
- Apply proper access controls and authentication
- Document and audit all mirroring activities
Q: What are the legal considerations for network traffic monitoring?
A: Legal considerations vary by jurisdiction but generally include:
- Employee privacy rights and notification requirements
- Data protection regulations (GDPR, CCPA, etc.)
- Industry-specific compliance (HIPAA, PCI-DSS, SOX)
- Lawful interception requirements for telecommunications
Always consult legal counsel before implementing comprehensive traffic monitoring.
Advanced Configuration Questions
Q: How can I implement failover for critical mirror sessions?
A: Implement redundant mirroring using multiple sessions and monitoring tools:
! Primary mirror session
Switch(config)# monitor session 1 source interface Gi1/0/10
Switch(config)# monitor session 1 destination interface Gi1/0/47
! Backup mirror session to different analyzer
Switch(config)# monitor session 2 source interface Gi1/0/10
Switch(config)# monitor session 2 destination interface Gi1/0/46
! Use EEM for automatic failover detection
Switch(config)# event manager applet MIRROR_FAILOVER
Switch(config-applet)# event syslog pattern "Interface GigabitEthernet1/0/47.*down"
Switch(config-applet)# action 1.0 cli command "configure terminal"
Switch(config-applet)# action 2.0 cli command "no monitor session 1"
Switch(config-applet)# action 3.0 cli command "monitor session 1 source interface Gi1/0/10"
Switch(config-applet)# action 4.0 cli command "monitor session 1 destination interface Gi1/0/46"Q: Can I modify mirrored packets before sending them to the analyzer?
A: Some advanced switches support packet modification features:
- Header stripping to reduce packet size
- VLAN tag insertion for traffic identification
- Timestamp addition for precise analysis
- Truncation to capture only headers
! Configure packet truncation for header-only analysis
Switch(config)# monitor session 1 source interface Gi1/0/15
Switch(config)# monitor session 1 destination interface Gi1/0/48 encapsulation replicate truncate 128Conclusion
Port mirroring remains a cornerstone technology for network visibility, security monitoring, and performance optimization in 2025. As networks continue evolving toward cloud-native, software-defined, and AI-driven architectures, port mirroring capabilities are adapting to meet new challenges while maintaining their fundamental value proposition of non-intrusive traffic observation.
The key to successful port mirroring implementation lies in understanding your specific monitoring requirements, properly sizing infrastructure components, implementing appropriate security controls, and following industry best practices. Whether you’re troubleshooting network performance issues, implementing security monitoring, meeting compliance requirements, or optimizing application performance, port mirroring provides the traffic visibility foundation necessary for effective network management.
Modern network administrators must balance traditional port mirroring techniques with emerging technologies like cloud traffic mirroring, AI-driven analysis, and software-defined networking integration. By staying current with technological developments and maintaining focus on operational excellence, organizations can leverage port mirroring to maintain robust, secure, and high-performing network infrastructures.
For organizations beginning their port mirroring journey, start with clear objectives, pilot implementations, and gradual expansion based on operational experience. Advanced users should focus on automation, integration with existing monitoring platforms, and preparation for next-generation networking technologies.
Remember that effective network monitoring is not just about capturing traffic—it’s about transforming that traffic data into actionable insights that drive business value and operational excellence.
Connect with network engineering insights and stay updated on the latest networking technologies. Follow @vinothrajat3
Stay threadsafe,
— Your friendly neighborhood backend whisperer 🧙♂️